Prerequisites
Device and hardware requirements
- A cable to connect to the device; either:
- A serial cable.
- An Ethernet cable. If you are using Ethernet, your device and host must be on the same network to be visible to each other.
- Mbed OS or Linux.
- See device and tool requirements on our website.
Using a pre-provisioned ATECC608A secure element
Device Management Client, Mbed OS and Factory Configurator Utility support the TrustFLEX-tier ATECC608A pre-provisioned secure element.
The secure element is a microprocessor chip pre-provisioned with keys and certificates that enable the DTLS handshake, which IoT devices and Device Management use to establish a secure connection. You can integrate pre-provisioned secure elements onto your board as an alternative to provisioning devices with secure credentials in the factory.
In production, you solder the secure element onto the board; however, Microchip offers evaluation kits, including the DM320118 development kit, which we use for the factory tool demo, as an example.
You can replace the default pre-provisioned credentials using Microchip's Trust Platform Design Suite, which enables you to generate a certificate authority (CA) and emulate the production flow of signing the pre-provisioned credentials on the secure element with your own CA.
The DM320118 development kit includes the CryptoAuth Trust Platform development board. To use the DM320118 development kit with the factory tool demo, you also need:
-
A K64F board.
-
Four male-to-male jumper wires to connect the K64F to the DM320118 development kit.
This is an example of how to connect the DM320118 to the K64F:
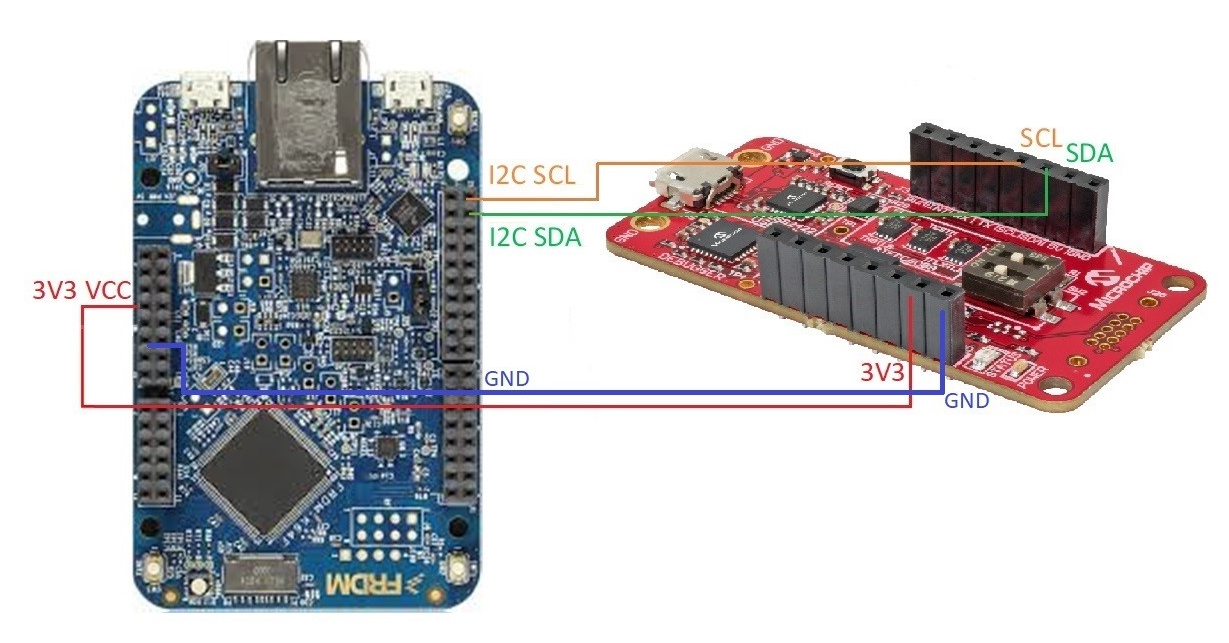
Note: To emulate the production flow of signing the pre-provisioned credentials with your own CA using Trust Platform Design Suite, before connecting the secure element to the K64F you must connect the DM320118 development kit to your computer to generate a CA, sign the credentials and replace the default credentials. You must then also copy the .c and .h files that you create as part of the process of generating the new credentials, and compile them with the FCC example, as described in Generating keys and certificates for the demo.
Using Parsec (Platform AbstRaction for SECurity) APIs to work with a software trusted platform module (TPM)
Device Management Client supports the Parsec open-source initiative, which provides a platform-agnostic interface for calling the secure storage and operation services of a trusted platform module (TPM) on Linux.
This lets you generate the device's bootstrap private key on a TPM during the factory flow. Later, when the device calls the Device Management bootstrap server, Device Management Client calls the Parsec API and uses the bootstrap key as part of the DTLS handshake, without having to export the key.
For the factory tool demo, we use IBM's Software TPM emulator on Linux x86. For information about integrating Device Management Client with Parsec on a hardware TPM, please contact us.
To use the TPM emulator with the factory tool demo:
- Install and run IBM's Software TPM, as explained on the Parsec documentation website.
- Install and run Parsec on your machine, as explained on the Parsec documentation website.
Note: You can only work with Device Management Client in production mode when you use Parsec and a TPM.
Working environment requirements
- Operating systems: We regularly verify that the demo works correctly on Windows 10 and Linux Ubuntu 18.04.
- Python 3.6-3.9 to run Factory Configurator Utility.
- Python 3.6.5 and later for the FCC example.
- Factory Configurator Utility.
- Mbed CLI.
- A supported compiler. See the supported compilers in Arm Mbed tools.
- (Optional) Trust Platform Design Suite to work with the ATECC608A secure element and emulate the production flow of signing the pre-provisioned credentials with your own CA.
Accounts
- A Device Management account (to download FCU).
- A GitHub account (to clone the FCC example).