How SDA works
Izuma Device Management secure device access (SDA) implements the ACE-OAuth standard, which specifies a framework for authenticating and authorizing in constrained Internet of Things (IoT) environments.
SDA has three components:
- An IoT device. The device runs an application that uses the SDA Client API to receive messages from a user device. The IoT device doesn't need to be connected to Device Management while using SDA.
- An SDA technician application on a user device, such as a mobile phone or tablet. The application uses the SDA Proxy API to message both Device Management and the IoT device.
- The authorization service (AS) on Device Management, which provides user and policy management services and provides permission in the form of an access token, so the user can securely access the IoT device.
This diagram illustrates the main elements and key concepts in SDA, and more details are below:
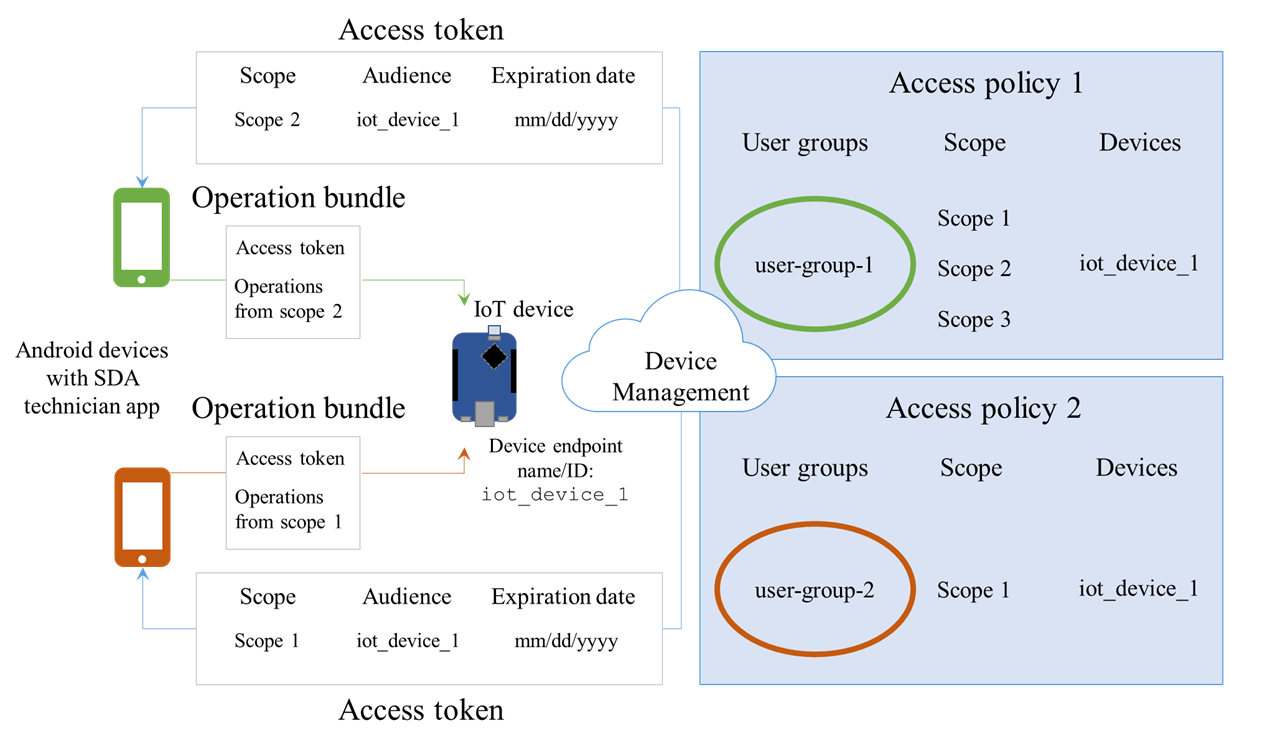
Access token
To access an IoT device, a user sends a request from the SDA technician application on their mobile device to Device Management. If the user meets the criteria of the policy, the Authorization Service (AS) running on Device Management returns an access token. The message (operation bundle) to the IoT device must include this access token, so the device can determine whether it must perform the specified operations.
The access token is a CBOR Web Token (CWT), which includes:
- An expiration date set in seconds (determined by the policy that generated the token).
- An audience, which defines the list of IoT devices the user has permission to access using the access token. The devices are identified by either their endpoint (assigned during the factory provisioning process) or a device ID (if the device has bootstrapped and connected to Device Management).
- A scope, which is a collection of operations (called functions in Device Management Portal) that the user has permission to perform. The device checks that the operation requested by the user is included in the scope of the access token. For example, a senior maintenance engineer may have permission to perform all operations, while a junior engineer may only have permission to perform a subset of operations. A scope can contain as many operations as required, but you can only have between one and twenty scopes per access token. You define a scope as part of an access policy.
Note: You must synchronize the list of operations that a technician can request. The operations must be the same in the code of your IoT device and SDA technician applications, and in your Device Management account.
Operation bundle
After the SDA technician application has permission to access the IoT device, it generates an operation bundle. This is a message that contains:
- An access token.
- The operations the user wants to perform.
Access policy
An access policy determines whether an individual has permission to access an IoT device and perform a certain operation (function). A policy includes:
- The scope of operations (functions) an authorized individual can perform.
- A list of the devices (as either endpoints or device IDs) the policy includes.
- A list of users that have permission to access these devices to perform the specified operations. This can be expressed as either individual users or as groups defined by the Device Management account team, or a mixture of both.
As an additional security measure, you can define how long an access token is valid. You can select an expiration time from one hour to two weeks.
The section on Setting up users and policies provides instructions on how to set up a policy.
Trust anchor
A trust anchor is a key-pair that links an IoT device to your Device Management account. Device Management uses the private key to sign the access token it generates for the SDA technician application. Inject the public key into the IoT device during the factory provisioning process.
If SDA has been enabled on your account (available on commercial accounts), a trust anchor is created automatically. You can find the trust anchor on the Device Management Portal by selecting Device identity > Trust anchor from the side menu.
Users and groups
An access policy gives permission to an individual to access an IoT device. When you configure a policy, you can specify individual users or groups of users. This enables you to create multiple policies, each tailored to the access the user requires.
The policy is stored in Device Management and not on the IoT device itself; therefore, you can remove a user's permissions simply by editing the policy or removing the user from your Device Management account, rather than by blocking all access to the IoT device.
You can set up users and groups in the portal, as explained in the sections about creating users and creating user groups.